The world is in the midst of a new major technological revolution. Specifically, this is the third major technological revolution in 35 years. Since the creation of the World Wide Web in 1989, information has been put online and can be accessed around the world at the speed of electrical signals. This is the information revolution. Despite this major innovation, information is largely unstructured and difficult to access. In the late 1990s and early 2000s, online information became more structured. Advanced search engines, such as Google, came online. Social media sites like Myspace and Facebook came online. This is the data revolution. Information has become more accessible, structured and rich, but large amounts of raw data are difficult to manage, classify and transform into actionable intelligence. From the late 2000s to the present, innovations such as online crowdsourcing, advances in artificial intelligence, facial recognition, social media data mining, and gamification have enabled large amounts of data to be processed into intelligence quickly and efficiently. This is the intelligence revolution.
These technological advances not only enabled an intelligence revolution but also enabled governments to deploy vast capabilities never before possible. When mass surveillance technology, advanced targeting systems, autonomous drones, and advanced artificial intelligence are combined, governments can create a lethal capability that exceeds even Orwell’s worst predictions. In other words, governments can create automated genocidal systems. How does such a system work?
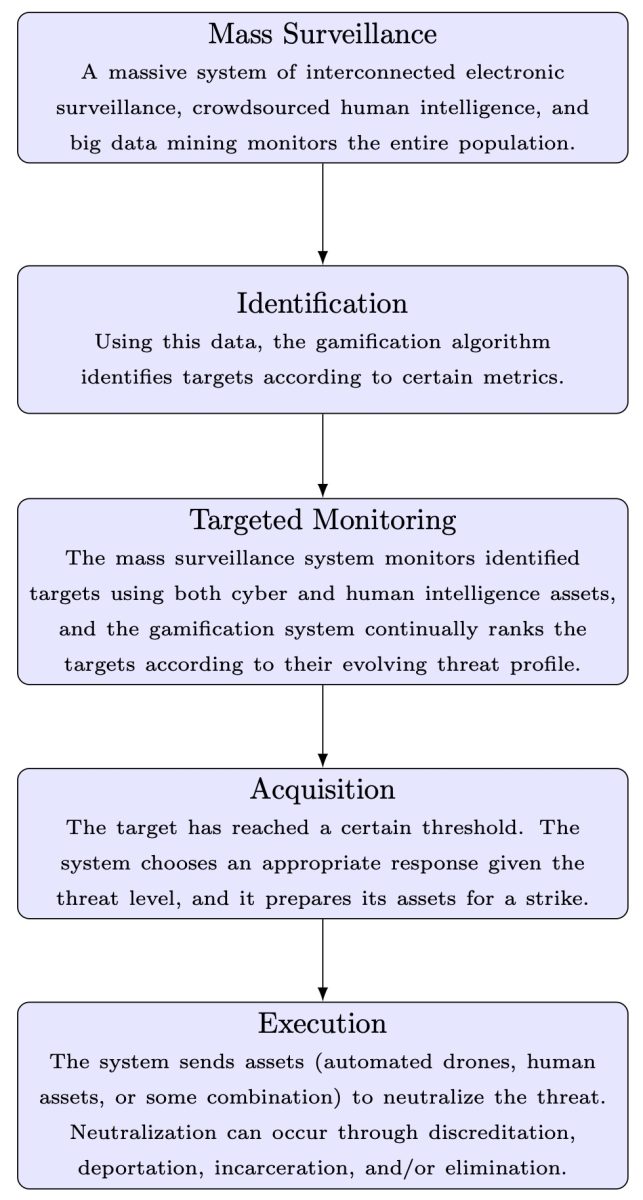
The first stage of an automated genocide system is mass surveillance, whether on physical or cyber battlefields. Mass surveillance technology can link a large number of cameras over a very wide geographical area to monitor an entire population. Through facial recognition, countries can easily identify and track people using these mass surveillance systems. China is currently using this technology in Xinjiang to identify and monitor Uyghurs, with horrific results. Israel uses a mass surveillance system called “Red Wolf” to track Palestinians through facial recognition.
Network data mining has also become more complex and powerful. Since the invention of the internet, governments have been using advanced data mining programs to monitor their populations. For example, the FBI’s Carnivore program was an early example of government data mining, and Carnivore’s capabilities were surpassed by the National Security Agency’s PRISM program, which captured vast amounts of data from the Internet. The creation of social media has only made this process easier. Bots and other advanced scraping tools guided by artificial intelligence can easily mine countless social media profiles, posts, and other media to gather intelligence on dissidents and political activists.
Cambridge Analytica demonstrated the power of data mining software by mining 87 million Facebook profiles during the 2016 presidential election. LinkedIn, Facebook, and Twitter profiles alone contain a wealth of information: name, address, locations visited, phone number, email, profile picture (used for facial recognition), education, work location, and names of colleagues and friends . Social media profiles also contain information that could serve as various indicators of the government’s search for dissent: connections with other dissidents (Facebook friends, LinkedIn connections, Twitter followers, etc.), tweets, Twitter hashtags, and Facebook comments. Mass surveillance systems can use social media data to build vast social network maps and profiles of political dissidents.
However, mass surveillance involves more than just cameras, network data mining and electronic listening devices. Human intelligence (HUMINT) still plays a vital role in any large-scale surveillance system, and technology can make the collection of HUMINT more effective and efficient through crowdsourcing. Crowdsourcing is the use of large numbers of people to collect information through online platforms. Through crowdsourcing, governments can quickly and efficiently gather intelligence from thousands, hundreds of thousands, or even millions of informants. Crowdsourcing also allows governments to direct large groups of supporters to respond to online dissent. The Israeli government has developed an online program called Act.il that helps coordinate “…thousands of volunteers primarily in the United States who can be directed from Israel to social media groups.” The app Programming allows the Israeli government and its allies to promote their narrative and effectively respond to any counter-narrative.
Using this data, governments can identify dissidents, opposition political activists, and any other groups that may pose a threat to the regime. Using a gamification system (similar to the social credit system used in China), these people can be ranked based on many different indicators (such as relationships with other dissidents, cooperation with dissident groups, participation in protests, etc.) to determine their threat level. Through this ranking, governments can focus their mass surveillance systems on specific individuals for ongoing surveillance. As more intelligence enters the system, each target’s individual ranking may change based on the target’s changing threat profile.
Once a targeted individual reaches a certain ranking, the system will automatically begin developing a plan to neutralize the threat. At a lower threshold, the system might simply send bots to attack the target’s social media accounts. If the threshold is high, the system may send security forces to imprison or deport the target. At its highest threshold, the system can dispatch autonomous drones to assassinate targets using state-of-the-art “swarm drone” technology.
This type of system is called an automated kill chain, and it’s not science fiction. The U.S. military has been developing the technology for years to fight Al Qaeda and Islamic State militants. Israel has deployed an automated kill chain called “Lavender” in Gaza. Lavender combines data mining with gamification algorithms to rank and designate targets for bombings and assassinations. Daddy, another system deployed by Israel in Gaza, uses integrated mass surveillance to track targets. The Ukrainian government is using an automated kill chain program called MetaConstellation. MetaConstellation combines “…commercial and classified government data…to enable military officials to communicate enemy locations to ground commanders or determine strike targets.”
Currently, the steps of the kill chain still involve some degree of separation and human involvement at each stage. For example, Israel’s “Lavender” target ranking system is separate from its “Where’s Dad” activist tracking system, which still requires human commanders to order drones or other military assets to strike. Fully automating the kill chain would require an advanced artificial intelligence capable of efficiently processing large amounts of data, and it was only a matter of time before someone developed the artificial intelligence needed to run such a system.
When such a powerful and dangerous weapon became feasible, its creation was almost inevitable. When countries begin deploying fully automated kill chain systems, these systems will simultaneously monitor, target, and neutralize dissidents across entire populations. Yes, humans will still be involved in intelligence collection and analysis at every stage of the kill chain, but the process from data exploration to target acquisition to execution will be automated.
These automated genocidal systems will be 21Yingshi The new weapon of mass destruction of the century. Unlike the indiscriminate destruction of nuclear weapons, automated genocide systems can be highly targeted by targeting tens, hundreds of thousands, or even millions of specific people belonging to specific groups (political dissidents, opposition groups, ethnic minorities, etc.) . In the six months since the war in Gaza broke out, Israeli forces have killed 33,137 Palestinians, many of which were caused by Israel’s “Lavender” and “Where Are We Going Dad” targeting systems. Imagine how high the death toll would be if the Israeli military had a fully automated kill chain.
Autogenocide is not just a concept from science fiction or Orwellian nightmares. Autonomous genocide is a product of the intelligence revolution and the result of the failure of international and domestic legal frameworks to regulate and curb the misuse of these emerging technologies. Technology capable of autonomous genocide is not theoretical; it is practical. These technologies have been developed and are currently being applied. The only missing piece is the integration of these technologies with artificial intelligence to enable a fully automated kill chain. The integration of artificial intelligence, crowdsourcing, gamification software, facial recognition and swarm drone technology will allow governments to kill with a speed and efficiency unprecedented in the history of the world. Without the establishment of a global regulatory body to oversee the development and proliferation of these destructive tools—as the world does with nuclear weapons—the world faces the proliferation of a terrifying new type of weapon of mass destruction.
figure 1
Further reading on electronic international relations

